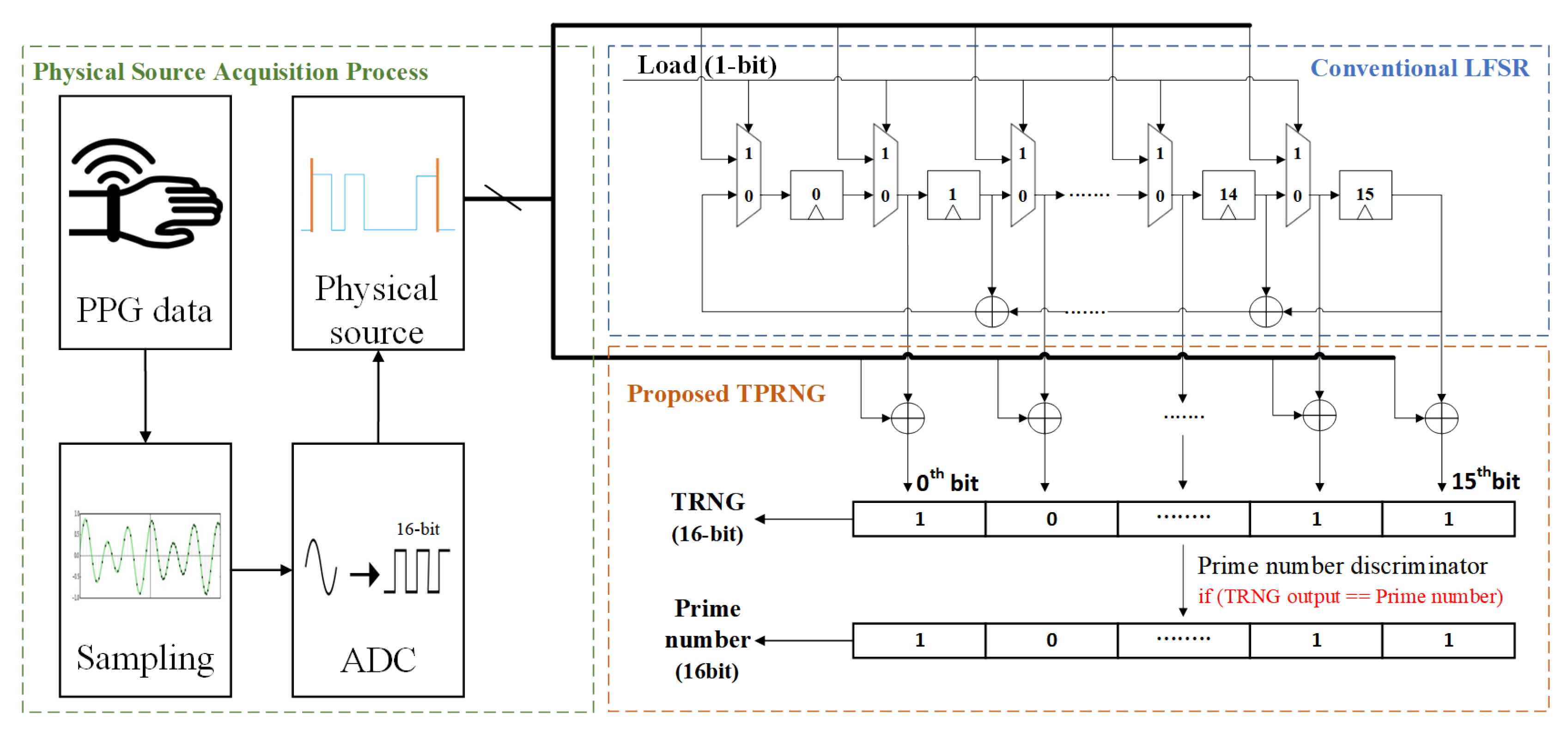
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices

An improved random bit-stuffing technique with a modified RSA algorithm for resisting attacks in information security (RBMRSA) - ScienceDirect

Generalized RSA using 2k prime numbers with secure key generation - Lone - 2016 - Security and Communication Networks - Wiley Online Library
RSA Public Key Encryption – The Code that Secures the internet | IB Maths Resources from Intermathematics

For Your Online Security: Thank Miller and Rabin | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium